

To create your own Digital Certificate you must telnet to your server and login as the administrator. Once logged in, type makecertificate. This command will create a new Digital Certificate which will enable your secure-server.
As an example, we will create a digital certificate for securenetworks.com.au
root:/www/https-conf# makecertificate
Digital Certificate Utility ---------------------------
This utility is used to create Digital Certificates for your Secure-Web Server.
When you create your Digital Certificate, you will have to answer a series of questions - please fill in all fields correctly as this information is displayed in the Web Browser if a user chooses to examine the Digital certificate. Changing directory to /www/https-conf
Step one - create the key and request:
Using configuration from /usr/local/ssl/lib/ssleay.cnf Generating a 1024 bit RSA private key ............................+++++ ............................+++++ writing new private key to 'privkey.pem' Enter PEM pass phrase: Verifying password - Enter PEM pass phrase: ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:AU State or Province Name (full name) [Some-State]:NSW Locality Name (eg, city) []:Sydney Organization Name (eg, company) []:Secure Networks Inc Organizational Unit Name (eg, section) []:IT Dept Common Name (eg, YOUR name) []:192.168.173.200 Email Address []:secure@securenetworks.com.au
Step two - remove the passphrase from the key:
read RSA private key Enter PEM pass phrase: writing RSA private key Step three - convert request into signed cert:
Signature ok subject=/C=AU/ST=NSW/L=Sydney/O=Secure Networks Inc/OU=IT Dept CN=192.168.173.200/Email=secure@securenetworks.com.au Getting Private key
The following has been added to your /www/https-conf/https.conf file SSLCertificateFile /www/https-conf/new.cert.cert SSLCertificateKeyFile /www/https-conf/new.cert.key
Successfuly created Digital Certificate!
root:/www/https-conf# ls -l total 46 -rw-r--r-- 1 root wheel 2676 Sep 21 09:16 access.conf -rw-r--r-- 1 root wheel 4722 Sep 21 09:20 httpsd.conf -rw-r--r-- 1 root wheel 2700 Sep 21 08:05 mime.types -rw-rw-r-- 1 root wheel 1001 Sep 21 09:53 new.cert.cert -rw-rw-r-- 1 root wheel 733 Sep 21 09:53 new.cert.csr -rw-rw-r-- 1 root wheel 887 Sep 21 09:53 new.cert.key -rw-rw-r-- 1 root wheel 963 Sep 21 09:53 privkey.pem -rw-r--r-- 1 root wheel 7744 Sep 21 09:16 srm.conf
Once you have created a Digital Certificate via telnet, open your web browser and connect to your secure-server.
NOTE: Web Browsers such as Netscape Navigator and Microsoft Internet Explorer will display error messages because the certificate has not been signed by a certified authority. Some Web Browsers (such as IE3.0) will refuse to connect to the secure-server as the certificate is not signed by an authority. It is highly recommended to purchase a digital certificate from either Twathe or Verisign.
When we first connect to the secure-server we are prestended with the dialog box below.
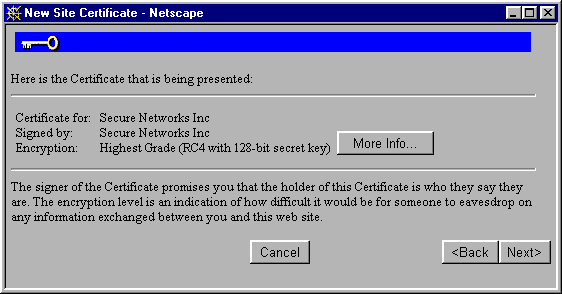
If you decide to purchase a Digital Certificate from either Twathe or Verisign, the web-browser will not alert the user about the certificate.
Once we approve the Digital Certificate we will connect to the secure-server
The online enrollment process for a Secure Server ID is very straighforward and can be accomplished in about 15 minutes. Once you have completed enrollment, your ID will be sent to you via e-mail in 1 to 3 business days.
Step 1: Confirm Domain
Name
VeriSign can only issue
a Secure Server ID to the registered owner of a domain name. In order for your
application to be processed, you will need to enter the exact domain name of
your Web site and the exact name of your site's registered owner.
VeriSign´s enrollment pages provide links to the local NICs that register domain names. Using these links, find your local NIC and use its whois service to verify ownership of your domain name.
Step 2: Obtain Proof
of Right
Before issuing your Secure
Server ID, VeriSign must confirm that your organization is legitimate and is
registered with the proper government authorities.
To avoid paperwork and speed processing time, you should submit your Dun & Bradstreet DUNS numbers. Your DUNS number will provide sufficient proof of your right to operate and use your company name. If you do business in the United States and you do not know your DUNS number, you can go to the Dun & Bradstreet site to search for it. You can also apply for a DUNS number at this site, if you do not have one.
If you do not conduct business in the United States, please contact your local Dun & Bradstreet representative to obtain your DUNS number. You can find a local representative through the Dun & Bradstreet Web site. Please note that international DUNS numbers must be in the Dun & Bradstreet database for at least two months before VeriSign can verify the information.
If you do not wish to use a DUNS number, you can fax or mail us any of the following documents when you complete on-line enrollment:
Digital ID Center
VeriSign, Inc.
1390 Shorebird Way
Mountain View, CA 94043
United States of America
Fax: (650) 961-8870
Step 3: Generate Private
Key and Certificate Signing Request
You now need to instruct
your SSLeay toolkit to generate a private key and a certificate signing request.
root:/www/conf# head -25 * > rand.dat
or
root:/www/conf#
ssleay md5 * > rand.dat
root:/www/conf# ssleay genrsa -rand rand.dat -des 1024 > key.pem
or, if you want to use triple DES:
root:/www/conf# ssleay genrsa -rand rand.dat -des3 1024 > key.pem
Note: Do not forget
your passphrase or your key will be unable to be used.
root:/www/conf# ssleay req -new -key key.pem -out csr.pem
where key.pem is the name of the key which you generated in step 2, and csr.pem is the name of the output CSR file.
You will be prompted for the following information:
-----BEGIN CERTIFICATE
REQUEST-----
MIIBETCBvAIBADBXMQswCQYDVQQGEwJBVTETMBEGA1UECBMKU29tZS1TdGF0ZTEh
MB8GA1UEChMYSW50ZXJuZXQgV2lkZ2l0cyBQdHkgTHRkMRAwDgYJKoZIhvcNAQkB
FgFgMFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBAL6nPTy3avNgbubx+ESmD4LV1LQG
fcSh8nehEOIxGwmCPlrhTP87PaA0XvGpvRQUjCGStrlQsd8lcYVVkOaytNUCAwEA
AaAAMA0GCSqGSIb3DQEBBAUAA0EAXcMsa8eXgbG2ZhVyFkRVrI4vT8haN39/QJc9
BrRh2nOTKgfMcT9h+1Xx0wNRQ9/SIGV1y3+3abNiJmJBWnJ8Bg==
-----END CERTIFICATE
REQUEST-----
Copy the entire contents of this CSR (including the BEGIN CERTIFICATE REQUEST and END CERTIFICATE REQUEST lines) and paste them into the enrollment form.
Step 5: Complete Application
Fill out the application
form with information about your organization and its contact people.
Step 6: Authentication
Takes Only 1-3 Days
VeriSign employees will
now examine the information that you have submitted. If everything is accurate,
you should receive your Secure Server by e-mail in a few days.
Your technical and organizational contacts will receive an e-mail confirming your order within a few hours of accepting the Secure Server Service Agreement and submitting your application. In the confirmation e-mail, you will receive a Personal Identification Number (PIN) and a URL where you can use that PIN to check on the processing status of your ID application.
Step 7: Install Your
ID
When your Digital ID is
approved, we will send it to your technical and organizational contacts by e-mail.
Your Server ID will look something like the following:
-----BEGIN CERTIFICATE-----
JIEBSDSCEXoCHQEwLQMJSoZILvoNVQECSQAwcSETMRkOAMUTBhMuVrM
mIoAnBdNVBAoTF1JTQSBEYXRhIFNlY3VyaXR5LCBJbmMuMRwwGgYDVQ
QLExNQZXJzb25hIENlcnRpZmljYXRlMSQwIgYDVQQDExtPcGVuIE1hc
mtldCBUZXN0IFNlcnZlciAxMTAwHhcNOTUwNzE5MjAyNzMwWhcNOTYw
NTE0MjAyOTEwWjBzMQswCQYDVQQGEwJVUzEgMB4GA1UEChMXUlNBIER
hdGEgU2VjdXJpdHksIEluYy4xHDAaBgNVBAsTE1BlcnNvbmEgQ2VydG
lmaWNhdGUxJDAiBgNVBAMTG09wZW4gTWFya2V0IFRlc3QgU2VydmVyI
DExMDBcMA0GCSqGSIb3DQEBAQUAA0sAMEgCQQDU/7lrgR6vkVNX40BA
q1poGdSmGkD1iN3sEPfSTGxNJXY58XH3JoZ4nrF7mIfvpghNi1taYim
vhbBPNqYe4yLPAgMBAAEwDQYJKoZIhvcNAQECBQADQQBqyCpws9EaAj
KKAefuNP+z+8NY8khckgyHN2LLpfhv+iP8m+bF66HNDUlFz8ZrVOu3W
QapgLPV90kIskNKXX3a
------END CERTIFICATE-----
root:/www/conf# getca hostname < /tmp/cert.tmp
Note: In some versions
of SSLEAY, you should use the command getversign instead of getca.
Your Secure Server ID
should now be saved as the file /www/conf/hostname.cert